Bitcoin Mining Slaves – the story of the miner botnet
Bitcoin Mining Slaves – the story of the miner botnet
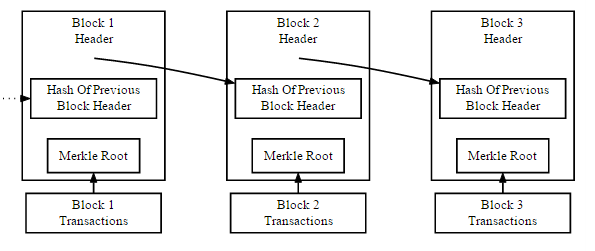
Bitcoin is a wonderful example of distributed computing. It is a digital crypto-currency built around a peer to peer network using open-source software. Created by the mysterious ‘Satoshi Nakamoto’, the Bitcoin system went live in early January 2009. All transactions are maintained in a public ledger called the ‘blockchain’ – which is made up of a series of sequential blocks in which each new block added references and refers to the previous created block – thus a ‘blockchain’.
Each new block comprises of a set of transactions containing details of payments made between Bitcoin users as well as a ‘proof-of-work’ since the last created block. The proof-of-work component requires that members of the network perform the repeated computation of a cryptographic hash function in order to discover an acceptable digital string based upon the SHA-256 standard – bundling together the new transactions since the last block into a newly created block
Usually, ‘mining’ for Bitcoins is performed using legitimate means, by members of the network dedicating their hardware resources. However, groups of illegally operating ‘miners’ have created botnets in order to surreptitiously harness and utilise the available processing power of thousands of unknowing PCs and mobile devices.
One such botnet injected multifunctional malware onto an unprotected device, so in addition to mining for Bitcoins it could generate additional revenue by stealing social network credentials, auctioning the provision of pay-per-install services to the highest bidder and be used for DDoS attacks.
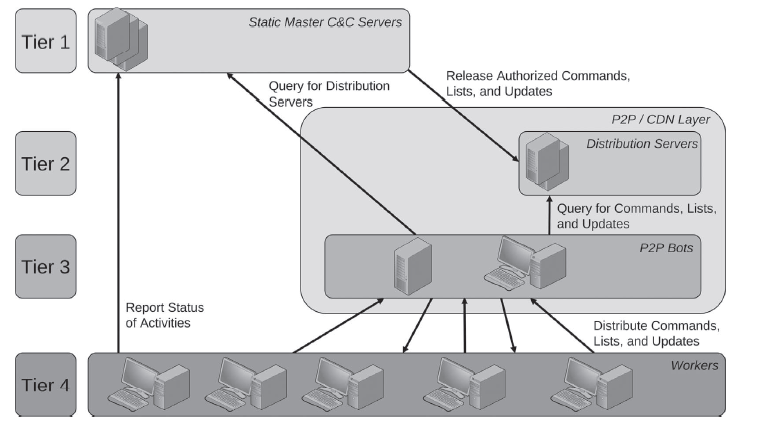
The malware operated on a 4 tiers – tier one comprised of command and control (C&C) servers, the second tier contained distribution servers that were trusted peers of the C&C servers, and also acted as fall-back servers for tier one in case the original C&C servers were taken down by law enforcement authorities.
Tier three’s function was to act as a content delivery network (CDN) distributing commands, lists and updates to tier four – who were the performing the role of mining slaves.
This botnet was so elegantly constructed, that it even benevolently downloaded the latest GPU driver updates on to the slave machines so as to better optimise the hash rates generated by their graphics cards. Updates to the malware occurred at a fairly regular frequency, furnished by tier three/the CDN. The CDN also provided status reports as well as data that had been extracted up to the tier two distribution servers. At its peak, the botnet was observed to have some 200,000 devices under its control, with an average of 23,000 available and online at any given time.
Putting the legality issues to one side, the botnet was an imaginative way of overcoming the computational difficulty in mining for bitcoins.
So the next time your phone overheats, or you find your PC running slowly, be aware that you could be an unwitting Bitcoin mining slave.

