Adventures in IT – an irregular blog

When Fear Holds the Wheel: How Some Institutions Use AI to Pretend, Not Perform
“We live in a time when the institutions that run society are struggling to cope with the complexities of the real world, and so they retreat into simplified versions of it.” Adam Curtis, HyperNormalisation 2016 Complexity makes people nervous. And when institutions get overwhelmed, they don’t reach for transparency — they reach for control. Or…
Fix Forward: What My Colleague Taught Me About AI Adoption
I used to work with someone who had a saying that drove some colleagues mad. He’d ship early. Launch things that weren’t quite ready. Roll out tools that still had visible rough edges. And every time someone pushed back, he’d say: “Let’s fix forward.” At the time, it felt uncomfortable. Risky, even. People wanted the…
Speed vs Depth: How System 1 Thinking Shapes AI Decisions at Work
Daniel Kahneman’s research on System 1 and System 2 thinking helps explain why some workplace decisions — especially around technology like AI — feel rushed or oversimplified. His model shows that we don’t always think in one consistent way. Instead, we alternate between two systems: In busy work environments filled with deadlines and pressure, System…
Ghosts in the Tech Stack – What Undead Tools Reveal About Leadership
“Every abandoned tool in your tech stack tells a story about a decision no one made” Most tech stacks aren’t pristine ecosystems. They’re haunted houses. Dig a little and you’ll find zombie applications no one uses, tools from vendors long forgotten, and shadow workflows left behind by employees who no longer work there. These aren’t…
Hacked by Hurry: How Forced Time Hijacks Your Prefrontal Cortex
We’ve got a group of students with us this week, shadowing different teams and working on a project about decision-making under uncertainty. After a few scenario discussions, one theme stood out: time pressure changes everything. That led me to reflect on something I’ve come to call forced time — when your natural pace of thinking…
Procurement Transformation in Action
Transforming procurement and supply chain operations requires more than just the right tools—it demands a clear strategy, strong leadership, and seamless execution. Hear from Adam Lalani, Chief Technology Officer, and Biju Raman, Procurement Director, at Alliad, on how YCP supported us in our Source-to-Pay (S2P) implementation and led a strategic procurement and supply chain optimization…
The Innovator’s Dilemma in Established Enterprises: Why Success Can Be Your Biggest Threat
Explore how established enterprises can fall into the trap of their own success, using Barnes & Noble’s response to the eBook revolution as a case study, and learn strategies to foster innovation and avoid disruption.
Podcast Interview with Threatspike Labs
Learn more about how I used Threatspike’s Blue service to protect our information assets
Strategic Mastery: How Cold War Game Theory Shapes the Modern CTO’s Edge
Introduction:The historical application of game theory during the Cold War unveils strategic principles that offer a distinctive advantage to today’s Chief Technology Officers. This exploration draws parallels between the intricacies of managing nuclear threats during the Cold War and the strategic considerations inherent in leading technology teams. By adapting lessons from historical analysts like Herman…
From Stress to Success: Optimizing Cognitive Resilience in Tech Leadership
Where innovation thrives, the positive influence of stress management on cognitive well-being becomes a cornerstone for CTOs. This perspective, inspired by a Harvard Health article, explores the optimistic facets of stress management, presenting strategies that not only shield our brains from the effects of stress but also enhance our cognitive capacities for sustained excellence in…
Tech Replicators: CTOs and the Evolutionary Power of Digital Ideas
Chief Technology Officers (CTOs) act as architects shaping the evolution of digital landscapes. Drawing inspiration from the evolutionary theories of William Hamilton and Richard Dawkins, this exploration delves into how CTOs can harness the power of digital ideas, akin to genes, to drive innovation, adaptation, and the transformative evolution of their technological ecosystems. Understanding Hamiltonian…
Breaking the Chains of Tech Hypernormality: Embracing Change in Persistent Environments
Quite often, teams can unwittingly fall into a state of “tech hypernormality,” a condition where the team operates in a seemingly stable environment despite underlying issues and the need for innovation. Much like the societal dynamics of hypernormalisation explored by Alexei Yurchak, tech hypernormality in a team setting occurs when the status quo is maintained,…
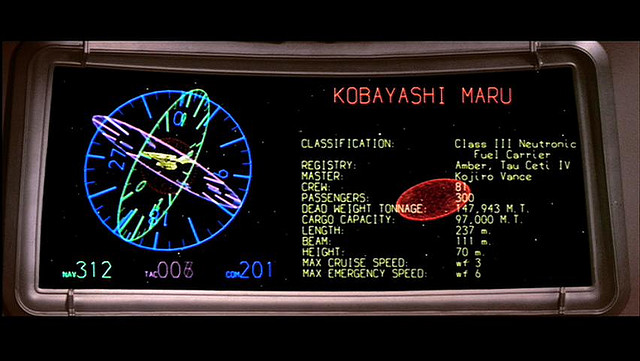
Bricolage and Beyond: Turning Unwinnable Tech Challenges into Triumphs
In the vast expanse of technology leadership, challenges often arise that mirror the infamous Kobayashi Maru scenario from Star Trek—a test designed to assess the resilience and creativity of Starfleet officers in the face of a no-win situation. Similarly, Chief Technology Officers (CTOs) find themselves navigating their own versions of the Kobayashi Maru, where tight…
Close Quarters, Big Gains: Unleashing Propinquity Power in Tech Leadership
After a recent optimisation workshop with one of our business units I realised that propinquity theory takes center stage as a guiding principle that can significantly impact organizational dynamics. If you are a CTO, understanding and strategically leveraging propinquity can lead to transformative improvements in people, processes, and products within the company. What is Propinquity…
The siege of the Great Library of Alexandria – the world’s first Cyberattack?
The Great Library of Alexandria is often seen as a tragic loss in history. But what if we view its destruction as an early form of cyber warfare? Looking back, the library was a hub of ancient knowledge, storing scrolls from various civilizations. Instead of chalking up its demise to accidents or conflicts, consider the…
Daring Experimentation as a CTO – Coltrane style
In the realm of technological leadership, picture the CTO as a maestro, drawing inspiration from the unparalleled jazz saxophonist, John Coltrane. The innovative improvisation characteristic of this maverick jazz genius offers an intriguing analogy. Coltrane, a luminary in the world of avant-garde jazz, was renowned for pushing the boundaries of traditional jazz norms. Similarly, a…
From Ancient Prophecies to Modern Preparedness: BCP with Cassandra’s Insight
In the annals of Greek mythology, Cassandra was renowned for her gift of prophecy, a blessing that often came intertwined with a curse—her prophecies were never believed. Her tragic story finds an unexpected resonance in the world of modern business continuity planning (BCP) and disaster recovery (DR). The lessons we can draw from Cassandra’s experience…
Commodifying Identity: The Digital Age’s Hidden Reality
In her 1994 essay, “Pandora’s Vox: On Community in Cyberspace,” Carmel Hermosillo astutely observes that the advent of computer networks and the digital age has not necessarily resulted in a reduction of hierarchy or the democratization of information. Instead, she sheds light on how these technological advances have led to the commodification of personal identity…
The Iron Horse and the Digital Age: Linking Past and Present
The late 19th century marked a remarkable period in American history with the construction of the transcontinental railroad, often referred to as the “Iron Horse.” This massive undertaking connected the East and West coasts, reshaping the nation’s transportation landscape and fostering economic growth. More than a century later, we find ourselves in another era of…
How can SMBs create a culture of curiosity and experimentation?
Leadership Engagement: The leaders within the SMB must set an example. When executives and managers show a genuine interest in exploring new ideas and technologies, it encourages the entire organization to follow suit. Encouraging Open Communication: Creating an environment where employees feel comfortable sharing their ideas, questions, and concerns is essential. SMBs can establish channels…
How your home router might be the backdoor in to your corporate network. Beware of the bear!
How your home router might be the backdoor in to your corporate network. Beware of the bear! As the world becomes increasingly connected, the line between personal and professional technology is becoming blurrier than ever. Many of us are now working from home, and that means our personal devices are being used for business purposes…
The Art of Inheritance – Get It Wrong and You’ve Lost Before You’ve Even Started
The Art of Inheritance – Get It Wrong and You’ve Lost Before You’ve Even Started When you join a new organisation or you are promoted to a leadership position you will often inherit a team that is already in place. They will certainly have far more experience of the nuances and intricacies of the organisation…
How to do Tech with heart
How to do Tech with heart Sometimes it’s good to reflect on some of the good things you’ve done, the lives you’ve touched, and why we work in the technology space. I’m happy to share a recent podcast episode I was interviewed for, hosted by Zoe Griffiths, the CEO of Alchemy of Learning, to deep…
Junkyard Tornado – why you need to get your house in order before going for Digital Transformation
Junkyard Tornado – why you need to get your house in order before going for Digital Transformation “…complex structures do not arise in a single evolutionary step…” – John Maynard Smith Nobody in their right mind believes that if a tornado swept through a junkyard it would assemble a Boeing 747. Yet, many organisations and…
IT Strategy with Donald Rumsfeld
IT Strategy with Donald Rumsfeld In a 2002 Department of Defense brieifing held by Donald Rumsfeld, then Secretary of Defense, regarding WMDs, he stated “there are known knowns; there are things we know we know. We also know there are known unknowns; that is to say we know there are some things we do not…
Hi res audio? Just gimme some truth.
Hi res audio? Just gimme some truth. The audio world has long been a place where small incremental upgrades have been seen (or heard lol) to make a difference to the quality of what one is hearing. Cables, amps, power filters – the list of ways to improve your playback experience is endless. Apple’s recent…
Bluffer Syndrome – How do unqualified people get into technology leadership positions?
Bluffer Syndrome – How do unqualified people get into technology leadership positions? When I left a previous role I was able to meet my successor on the way out. I knew in 5 minutes that this guy wasn’t going to make it. How did I know but those that chose him didn’t? The answer is…
Bitcoin Mining Slaves – the story of the miner botnet
Bitcoin Mining Slaves – the story of the miner botnet Bitcoin Mining Slaves – the story of the miner botnet Bitcoin is a wonderful example of distributed computing. It is a digital crypto-currency built around a peer to peer network using open-source software. Created by the mysterious ‘Satoshi Nakamoto’, the Bitcoin system went live in…
You won’t find drones delivering pianos anytime soon
How drones will reshape Middle East enterprises How many neglected online shopping carts are a result of expensive shipping costs and lengthy delivery times? Eighty-six percent, according to management consulting group McKinsey & Group. That’s a staggeringly high percentage, and one that should act as a sure-fire cause for retail firms to explore alternative methods…
Why Blockchain’s only limit is human imagination
Why Blockchain’s only limit is human imagination Back in the mid-90s when I first had access to the Internet, I couldn’t really understand what the hype was all about. I was a gamer in those days, so my first use case for the Internet was to find WAD files – custom maps, weapons and characters…